Microsoft loves to promote Windows 11 25H2’s AI features and other improvements, but can it actually game...
The Audio-Technica ATH-R50x look and sound great, and they benefit from their open-ear design in ways that...
While Apple Silicon Macs natively only support macOS, that hasn’t stopped enthusiasts from finding a way to...
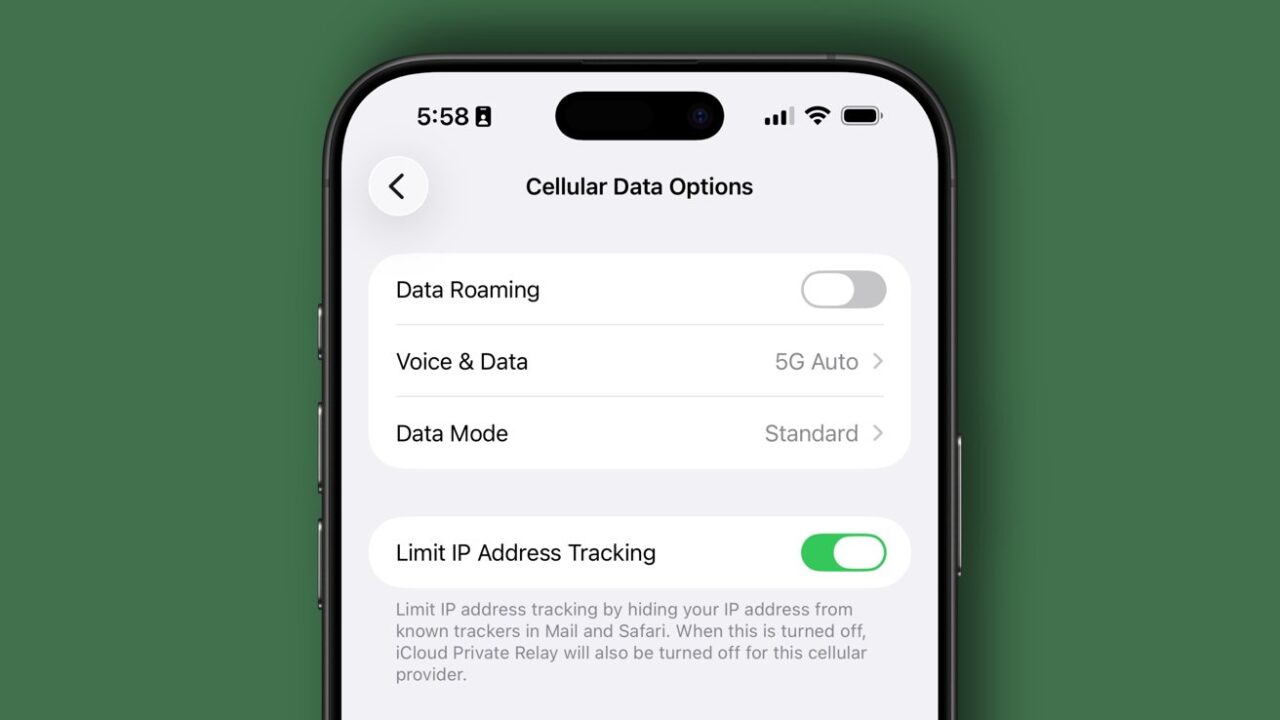
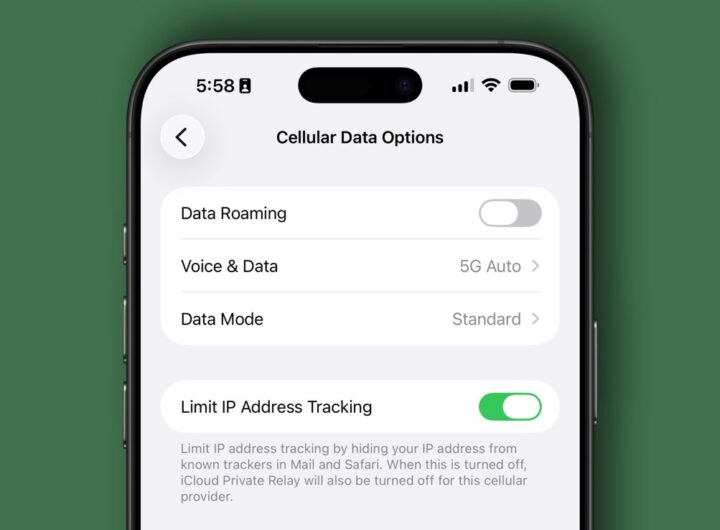
A user’s location data is incredibly sensitive information, and while it can be kept from apps on...
A team at Rice University has developed a new material for filtering per- and polyfluoroalkyl substances (PFAS)....
One of the biggest constraints currently facing AI builders who want to deploy agents in service of...
Anthropic announced Monday that users can now open and interact with popular business applications directly inside Claude,...
Your web gateway can’t see it. Your cloud access broker can’t see it. Your endpoint protection can’t...
When Anthropic announced Monday that it was embedding nine workplace applications directly inside Claude, transforming its AI...
Presented by Insight Enterprises Organizations today are trapped in proof-of-concept purgatory because yesterday’s models don’t work for...