Spying through Push Notifications

Spying through Push Notifications: A Hidden Vulnerability

Push notifications seem harmless, those little pop-ups on your phone keeping you updated, right? But what if they were being used to spy on you? This is the unsettling reality raised by recent reports about governments and potentially malicious actors exploiting push notifications for surveillance.

Here’s how it works:
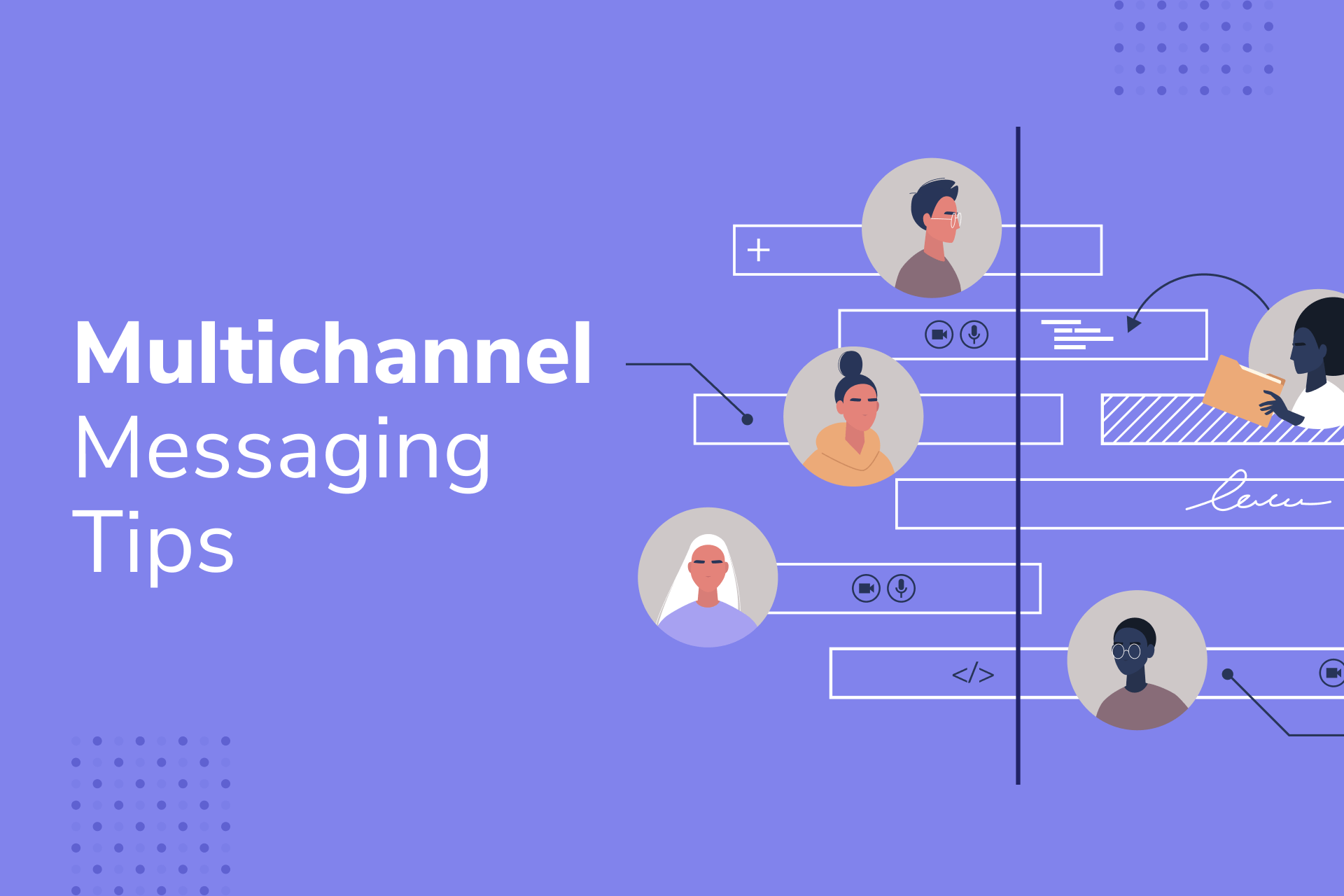
- Intermediary Servers: When you receive a push notification, it isn’t directly sent from the app. It goes through Apple’s or Google’s servers first, acting as a middleman. This gives them access to the notification data.
- Metadata Collection: While the actual content of the notification might be encrypted, the surrounding information (metadata) is often not. This metadata can reveal:
- Which app sent the notification: This can indicate your interests, activities, and even location.
- When the notification was sent: This could create a timeline of your activity.
- Device and account information: This can link the notification to your specific identity.
- Potential for Abuse: With this metadata, governments or attackers could:
- Track your movements: By analyzing notifications from location-based apps, they could build a picture of your daily routine and whereabouts.
- Monitor your interests and activities: Notifications from news apps, social media, or shopping platforms can reveal your political leanings, personal relationships, and even purchase habits.
- Target you with personalized disinformation: Knowing your interests, they could send you tailored fake news or propaganda disguised as notifications.
It’s important to note that:
- The extent of this spying is currently unclear. While reports exist, the scale and specific methods used remain under investigation.
- Not all push notifications are vulnerable. Some apps use end-to-end encryption on their notifications, protecting the content and metadata.
- There are ways to mitigate the risk. You can adjust your notification settings, choose apps with strong privacy practices, and use security tools to encrypt your data.
Spying through push notifications raises serious concerns about privacy and security. It is crucial for both tech companies and users to be aware of this vulnerability and take steps to protect themselves. By demanding stronger encryption and data minimization practices, we can fight back against unauthorized surveillance and uphold our right to privacy in the digital age.
Additional Resources:
- Schneier on Security: https://osintcorp.net/spying-through-push-notifications-schneier-on-security/
- Wired: https://twitter.com/WIREDScience/status/1732625014149550380
- Lifehacker: https://lifehacker.com/tech/governments-spying-on-push-notifications
When you get a push notification on your Apple or Google phone, those notifications go through Apple and Google servers. Which means that those companies can spy on them—either for their own reasons or in response to government demands.
Sen. Wyden is trying to get to the bottom of this:
In a statement, Apple said that Wyden’s letter gave them the opening they needed to share more details with the public about how governments monitored push notifications.
“In this case, the federal government prohibited us from sharing any information,” the company said in a statement. “Now that this method has become public we are updating our transparency reporting to detail these kinds of requests.”
Google said that it shared Wyden’s “commitment to keeping users informed about these requests.”
The Department of Justice did not return messages seeking comment on the push notification surveillance or whether it had prevented Apple of Google from talking about it.
Wyden’s letter cited a “tip” as the source of the information about the surveillance. His staff did not elaborate on the tip, but a source familiar with the matter confirmed that both foreign and U.S. government agencies have been asking Apple and Google for metadata related to push notifications to, for example, help tie anonymous users of messaging apps to specific Apple or Google accounts.

